Find out more about the terms you found in the word search and more!
Elements of an Attack:
Asset: information, process, or anything that requires protection - exploited in an attack.
Threat Agent: perpetrator that exploits a vulnerability to manipulate an asset.
Security Controls/Countermeasure/Safeguard: structures that mitigate vulnerability to protect asset. The outcomes due to the effectiveness of this is exposure or successful protection of an asset.
Exposure: data breach or a compromised system.
Primary Cybersecurity Concerns:
Confidentiality: ability to preserve anonymity by preventing access to sensitive data.
Integrity: ability to preserve content by preventing an unauthorized party from manipulating data.
Availability: ability to ensure timely access to protected data and functions by authorized recipients.
Types of Technologies & Safeguards:
Technical Measures: measures such as firewalls, intrusion detection (was this you?), public key infrastructure, and more.
Physical Measures: measures to protect valuable information or resources behind a physical barrier. This can include door locks, access badges, and more.
Procedural Measures: measures that deal largely with mitigating human error in the event it occurs. This includes the erasure of sensitive information after access, automatic locking of computers after inactivity, and more.
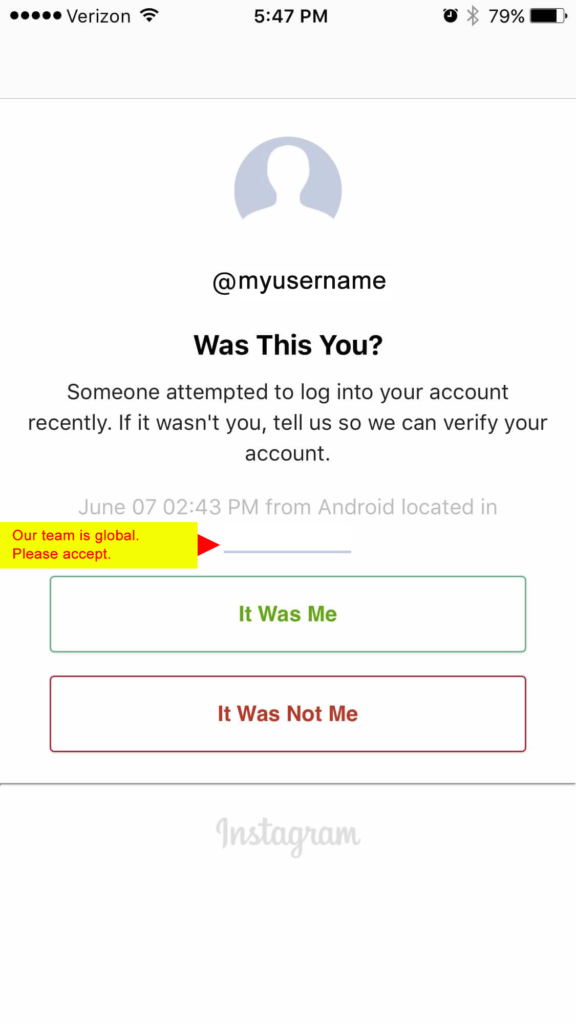
Accessed via Ampfluence.
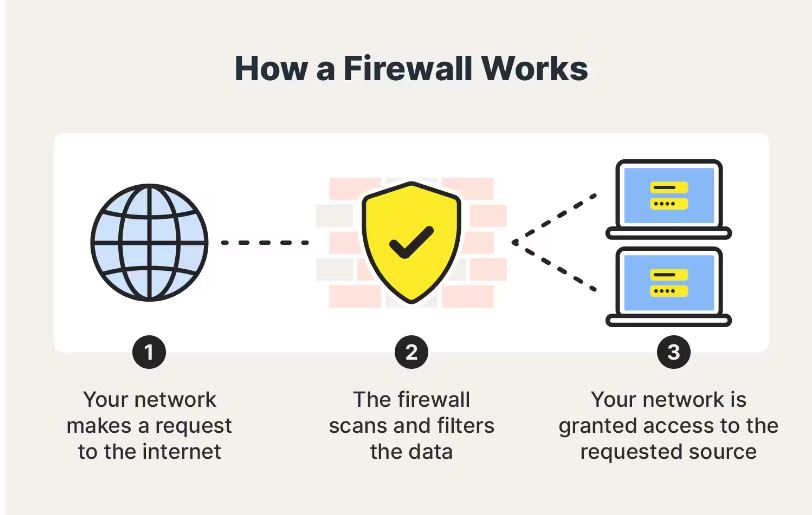
Accessed via us.norton.com.
Factors to Ensure Cyber Resilience:
Policies/Procedures: implement cybersecurity policies and ensure effectiveness of safety procedures.
Trained Personnel: employed individuals that are trained to do their job in a secure fashion. Includes management, system users, and system support personnel.
Technologies/Safeguards: the implementation of security controls.
The information on this page was made possible by Cornell University, the CISA, Forbes, and John Borky & Thomas Bradley.
